
According to Bleeping Computer, hackers targeted the FBI’s email servers, sending thousands of bogus messages claiming that recipients had been victims of a “sophisticated chain attack.” The Spamhaus Project, a non-profit that investigates email spammers, was the first to discover the emails.
The emails falsely claim that Vinny Troia was behind the bogus attacks and that Troia is linked to the notorious hacking group The Dark Overlord — the same bad guys who leaked the fifth season of Orange Is the New Black. Troia is a well-known cybersecurity researcher who is the founder of two dark web security firms, NightLion and Shadowbyte.
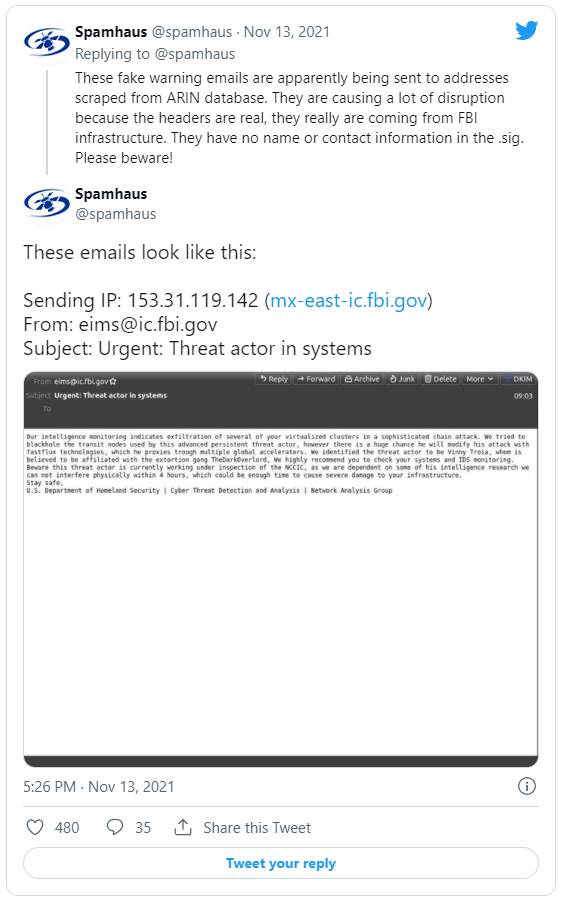
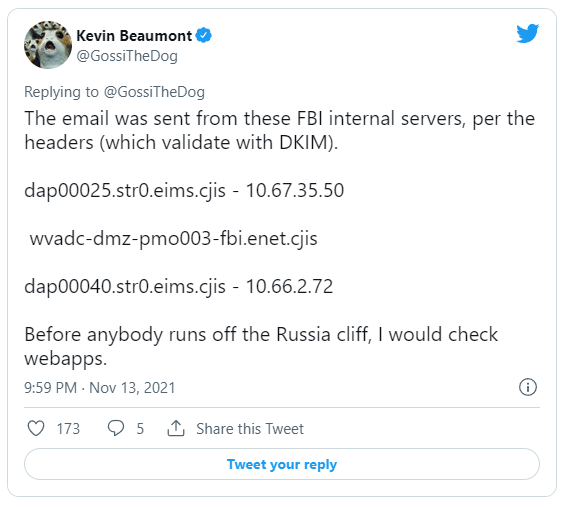
According to Bleeping Computer, the hackers were able to send emails to over 100,000 addresses, all of which were scraped from the ARIN database. According to Bloomberg, hackers allegedly used the FBI’s public-facing email system to make the emails appear more legitimate. According to cybersecurity researcher Kevin Beaumont, the headers are authenticated as coming from FBI servers using the Domain Keys Identified Mail (DKIM) process, which is part of the system Gmail uses to stick brand logos on verified corporate emails.
The FBI issued a statement in response to the incident, stating that it is an “ongoing situation” and that “the impacted hardware has been taken offline.” Other than that, the FBI says it has no additional information to share at this time.
According to Bleeping Computer, the spam campaign was most likely carried out to discredit Troia. Troia speculates in a tweet that the attack was carried out by a person known only as “Pompompurin.” According to Bleeping Computer, the same person has allegedly tried to harm Troia’s reputation in the past in similar ways.
Pompompurin is also linked to the incident, according to a report by computer security reporter Brian Krebs, who claims the individual messaged him from an FBI email address when the attacks were launched, saying, “Hi, its pompompurin.” Check the headers of this email; it’s coming from an FBI server.” KrebsOnSecurity spoke with Pompompurin, who claims that the hack was intended to draw attention to security flaws in the FBI’s email systems.
Pompompurin told KrebsOnSecurity, “I could’ve 1000 percent used this to send more legitimate-looking emails, trick companies into handing over data, etc.” According to the source, they took advantage of a security flaw on the FBI’s Law Enforcement Enterprise (LEEP) portal and used a one-time password embedded in the page’s HTML to sign up for an account. Pompompurin claims to have been able to manipulate the sender’s address and email body from there, allowing them to carry out the massive spam campaign.
With that level of access, the attack could have been far more serious than a false alarm that alerted system administrators. President Joe Biden mandated a bug fix earlier this month, requiring civilian federal agencies to patch any known threats. Following the devastating attacks on the Colonial Pipeline and SolarWinds, Biden signed an executive order in May aimed at improving the nation’s cyber defenses.




